Introduction
In the invisible infrastructure that connects our world, mobile networks constantly “talk” to each other to route calls and deliver text messages. Deep within this conversation lies a powerful command known as Any Time Interrogation (ATI). While originally designed to help network operators optimize service and locate subscribers for legitimate reasons, ATI has gained notoriety in cybersecurity circles. It is frequently cited as the “skeleton key” that allows surveillance companies and malicious actors to track mobile phone users across the globe without their knowledge.
Understanding Any Time Interrogation is no longer just for telecom engineers; it is essential for privacy advocates, cybersecurity professionals, and anyone interested in how mobile networks function and malfunction. This article demystifies the ATI command, exploring its technical mechanics within the Signaling System No. 7 (SS7) framework, its legitimate utility, and the critical security vulnerabilities that have forced the telecom industry to rethink network defense. We will dissect how a simple status query became a premier tool for digital espionage and what is being done to stop it.
What is Any Time Interrogation (ATI)?
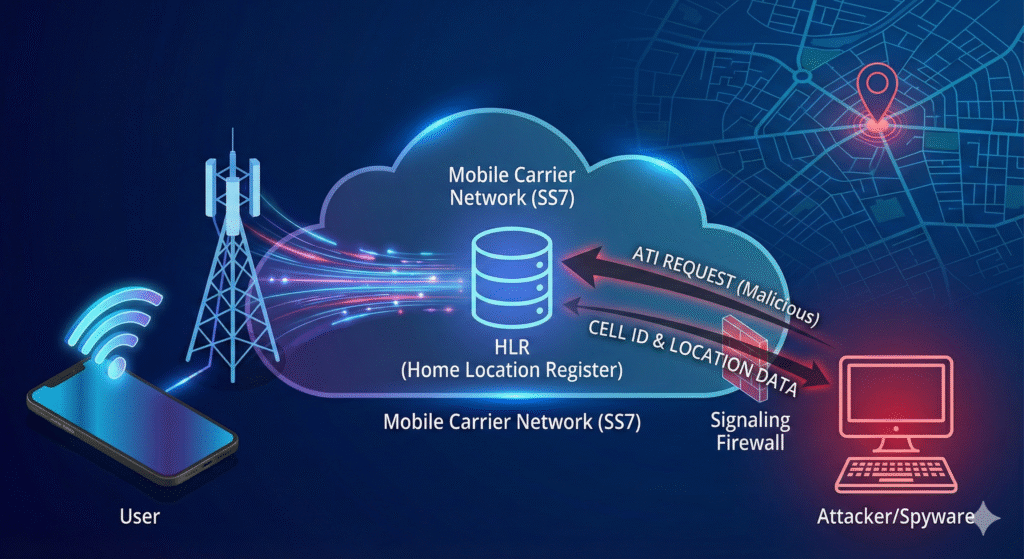
Any Time Interrogation (ATI) is a specific signaling message used in the Mobile Application Part (MAP) of the SS7 protocol suite. In simple terms, it is a digital question that one part of a mobile network asks another. Specifically, a service node (like a voicemail system or intelligent network platform) sends an ATI query to the Home Location Register (HLR) the central database that stores details about every subscriber in a network.
The purpose of this query is to retrieve up-to-the-minute information about a mobile subscriber. Unlike other queries that might wait for a user to make a call, ATI is designed to get data immediately hence the name “Any Time.”
- Protocol: SS7 (Signaling System No. 7) / MAP (Mobile Application Part).
- Target: HLR (Home Location Register).
- Data Retrieved: Cell ID (Location), Subscriber State (Busy/Idle), and IMEI.
The Mechanics: How ATI Works in the Network
To understand the power of ATI, one must visualize the architecture of a mobile network. When a query is initiated, it bypasses the phone itself; the user sees no notification, no battery drain, and no signal bar change. The interaction happens entirely at the network level.
The process typically follows these steps:
- Request Initiation: A GSM Service Control Function (gsmSCF) or an external node sends a
MAP-ANY-TIME-INTERROGATIONmessage to the subscriber’s HLR. - HLR Processing: The HLR receives the request. If allowed, it looks up the subscriber’s current status.
- VLR Query (Optional): If the HLR needs precise location data, it may query the Visitor Location Register (VLR) where the phone is currently roaming using a
ProvideSubscriberInfo(PSI) message. - Response: The HLR sends the requested data back to the inquirer. This data packet often contains the Cell Global Identity (CGI), which pinpoints the user’s location to a specific cell tower.
Legitimate Use Cases for ATI
Before it became a security pariah, ATI was and still is a highly useful network tool. Operators rely on it for seamless service delivery. It was not built for spying; it was built for efficiency.
- Intelligent Call Routing: Determining if a user is roaming to route a call through the cheapest path.
- Billing Systems: verifying a user’s location to apply correct roaming charges in real-time.
- Number Portability: Checking the status of a number before attempting to connect a call to a ported network.
- Voicemail Systems: Checking if a user is “busy” or “out of reach” to immediately divert a call to voicemail without ringing the network unnecessarily.
The Security Vulnerability: The “ATI Attack”
The vulnerability of Any Time Interrogation lies in the lack of authentication inherent in the legacy SS7 protocol. SS7 was built in the 1970s on a foundation of trust: it assumed that anyone connected to the global signaling network was a legitimate operator. Today, access to this network can be bought or leased, allowing hackers to send ATI commands from halfway across the world.
Attackers use ATI to perform Location Tracking. By sending an ATI request to a target’s HLR, the attacker receives the Cell ID. By mapping this Cell ID to a database of tower locations (available publicly), they can triangulate the user’s physical position within a few hundred meters.
- Silent Tracking: The victim never knows they are being located.
- Global Reach: An attacker in Country A can track a victim in Country B.
- Low Barrier to Entry: Requires only basic SS7 access and the victim’s phone number (MSISDN).
The Role of SS7 in ATI Exploits
Signaling System No. 7 (SS7) acts as the nervous system of the global telecommunications network. While 4G and 5G use newer protocols (Diameter and HTTP/2), SS7 is still used for 2G/3G networks and, crucially, for interconnecting different networks while roaming.
ATI exploits leverage the “interconnect” nature of SS7. An attacker disguises their computer as a legitimate network node (like a foreign carrier’s switch). The victim’s home network, programmed to trust SS7 messages, obliges the request and hands over the data. This flaw is not a “bug” in the software code but a fundamental architectural weakness of the protocol itself.
Real-World Impact: Espionage and Surveillance
The misuse of Any Time Interrogation has moved beyond theoretical research into active deployment. Surveillance companies often sell “geolocation services” to governments and private clients, which rely heavily on SS7/ATI exploits.
Notable Examples:
- The Pegasus Context: While spyware like Pegasus infects the phone, SS7 attacks like ATI tracking can be done without ever touching the device.
- Ukraine Conflict: Reports have surfaced of SS7 vulnerabilities being used to track soldiers’ movements by monitoring their mobile connections.
- Banking Fraud: By using ATI to determine if a user is roaming or active, attackers can time their SMS interception attacks (using other SS7 flaws) to bypass Two-Factor Authentication (2FA) for bank accounts.
Detecting and Blocking ATI Attacks
Telecommunication operators are now engaged in an arms race against these exploits. The primary defense against malicious ATI requests is the deployment of Signaling Firewalls.
A Signaling Firewall sits at the edge of an operator’s network. It inspects incoming SS7 traffic and filters out suspicious ATI messages.
- Category 1 Blocking: Blocking ATI requests from unknown or non-partner Global Titles (network addresses).
- Velocity Checks: Flagging multiple location requests for the same subscriber in a short period (a sign of active tracking).
- Home-Routing: Ensuring that location queries are not answered directly but are proxied or obfuscated to hide the actual Cell ID.
ATI vs. Provide Subscriber Info (PSI)
In technical discussions, ATI is often mentioned alongside another message: Provide Subscriber Info (PSI). While they are similar, there is a nuance in how they are weaponized.
| Feature | Any Time Interrogation (ATI) | Provide Subscriber Info (PSI) |
| Target Node | HLR (Home Location Register) | MSC/VLR (Mobile Switching Center) |
| Information Depth | General status, basic location | Precise location, active status |
| Attack Vector | Easier to execute (only need phone number) | Often requires spoofing HLR; harder |
| Blocking Status | Frequently blocked by modern firewalls | Harder to block without breaking roaming |
The Evolution: ATI in 4G (Diameter) and 5G
As the world moves to 4G and 5G, does Any Time Interrogation disappear? Not entirely.
In 4G (LTE), the SS7 protocol is replaced by Diameter. The equivalent of the ATI command in Diameter is the User-Data-Request (UDR) or Insert-Subscriber-Data (IDR). While Diameter has better security features (like IPsec), it still suffers from similar interconnect trust issues if not properly firewalled.
In 5G, the architecture shifts to HTTP/2 and JSON. However, because 5G networks often rely on 4G and 3G for fallback (voice calls and roaming), legacy SS7 ATI attacks remain a valid threat vector against 5G subscribers who drop down to older networks.
Best Practices for Mobile Privacy
For the average user, defending against network-side attacks like ATI is difficult because the vulnerability exists at the carrier level, not on the phone. However, high-risk individuals (journalists, diplomats) can take precautions.
- Use Encrypted Messengers: Apps like Signal or WhatsApp operate over the data layer, making SMS interception irrelevant.
- Disable 2G/3G: If your phone allows it, forcing “LTE Only” or “5G Only” can mitigate some SS7-based tracking, though not all.
- Flight Mode: The only surefire way to stop network interrogation is to disconnect from the network entirely.
Regulatory and Industry Response
The GSMA (Global System for Mobile Communications Association) has issued guidelines (FS.11) recommending that operators block inbound ATI messages from external networks unless there is a specific roaming agreement in place.
Regulatory bodies like the FCC in the US and ENISA in the EU are increasingly pressuring operators to secure their signaling networks. The era of “blind trust” in telecom is ending, and strict filtering of Any Time Interrogation messages is now a baseline requirement for network security compliance.
Conclusion
Any Time Interrogation is a classic example of a feature designed for utility that morphed into a weapon. It highlights the fragility of our connected infrastructure: a simple query command, intended to help route a phone call, can be abused to erode the privacy of millions.
As we transition into the 5G era, the lessons learned from ATI are shaping the future of network security. Operators are building thicker walls and smarter filters, but the legacy of SS7 ensures that ATI remains a relevant topic in cybersecurity. For now, it serves as a stark reminder that in the world of telecommunications, being “connected” means being “reachable” in more ways than one.
FAQs
Can I detect if someone is using Any Time Interrogation on my phone?
No, you cannot detect it on your device. ATI queries happen at the network infrastructure level (between the attacker and your mobile carrier’s database). The signals do not reach your phone, so there are no logs, notifications, or battery usage indicators to alert you.
Is Any Time Interrogation illegal?
The command itself is a legal and standard part of telecommunications protocols used for network management. However, unauthorized use of ATI to track someone’s location without their consent is illegal in most jurisdictions, classified as wiretapping, stalking, or unauthorized computer access.
Do VPNs protect against ATI location tracking?
No. A VPN encrypts your internet traffic (data layer), but ATI operates on the signaling layer (cellular network control). Even with a VPN, your phone must communicate with cell towers to maintain a connection. The network must know your location to route calls to you, and ATI exploits that necessity.
Why don’t operators just turn off ATI?
Operators cannot simply “turn off” ATI globally because it is used for legitimate internal functions like billing, call routing, and voicemail systems. Instead, they must implement “Signaling Firewalls” that intelligently distinguish between legitimate internal requests and malicious external ones.
Does Any Time Interrogation work on 5G networks?
Pure 5G (Standalone) uses different protocols (HTTP/2) and does not use ATI. However, most current 5G networks are “Non-Standalone,” meaning they rely on 4G/LTE and legacy infrastructure for core functions. Furthermore, if a 5G phone drops to 3G/2G for a call, it becomes vulnerable to SS7 ATI attacks.
What information can an attacker get with ATI?
The primary data retrieved is the Cell Global Identity (CGI), which identifies the specific cell tower your phone is connected to. By mapping this ID, an attacker can determine your location within a few hundred meters (urban areas) or kilometers (rural areas). It can also return the IMEI (device serial number) and subscriber status (busy/idle).How does a Signaling Firewall stop ATI attacks?
A Signaling Firewall sits at the perimeter of a mobile network. When an ATI request arrives from a foreign network, the firewall checks the source. If the request comes from a network with no roaming agreement or looks suspicious (e.g., high frequency), the firewall drops the packet or replies with fake data, protecting the subscriber.